Quora Poe 提供了多种 Chat AI,例如 GPT-3、GPT-4、Claude 等,相比 ChatGPT 的双向空气墙,Poe 单向墙更易于使用。
如果你会魔法,可直接访问官网使用 poe.com,本文记录如何使用 Nginx 反代 Poe
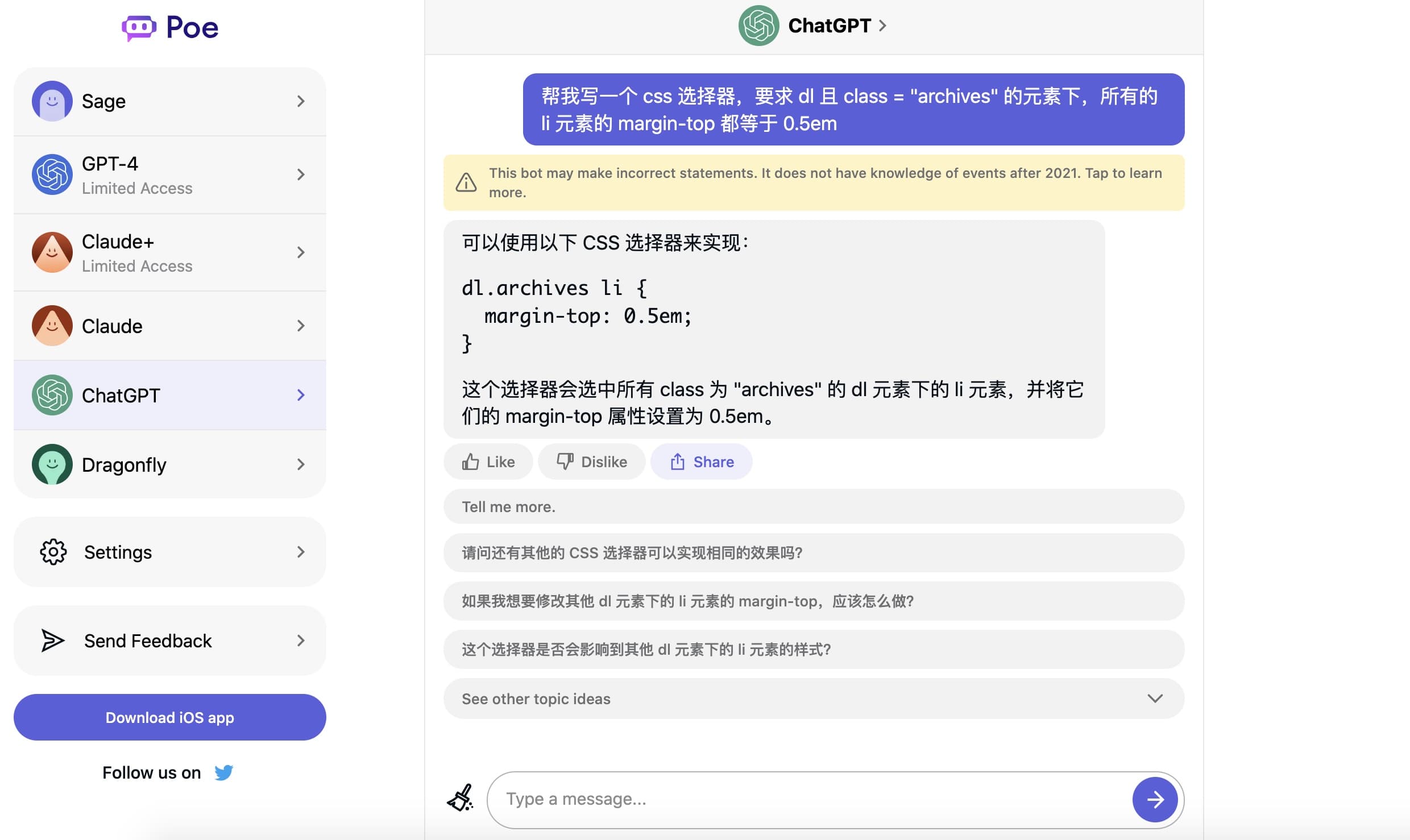
Nginx 配置
server {
listen 80;
server_name 150.230.77.88;
location / {
proxy_pass https://poe.com;
proxy_set_header Host poe.com;
proxy_set_header Connection "";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_ssl_verify off;
}
}
以上配置可以让服务器代为访问 Poe,但我建议你使用 HTTPS + 认证。
ZeroSSL IP 证书
没有域名的情况,那么推荐使用 ZeroSSL 申请一张免费的 IP 证书,有效期 3 个月。
验证的时候,选择上传文件的方式,这种方式只需要把 Zoro 提供的 txt 文件放置到机器指定目录下(如新建:.well-known/pki-validation/),上传验证文件到此目录
python3 -m http.server 80
使用 pyhton 临时启动个 http 服务,打开浏览器访问 http://150.230.77.88/.well-known/pki-validation/22258BBCF1816EDB976FF67CB29B5830.txt
能看到内容即可点击验证,选择下载 Nginx 类型的证书📄
压缩包包含三个文件 certificate.crt、ca_bundle.crt、private.key,在 Nginx 中使用前还需要处理下
$ cat certificate.crt ca_bundle.crt >> certificate.crt
上传到服务器指定目录供 Nginx 使用
ssl_certificate /etc/ssl/certificate.crt;
ssl_certificate_key /etc/ssl/private.key;
配置认证
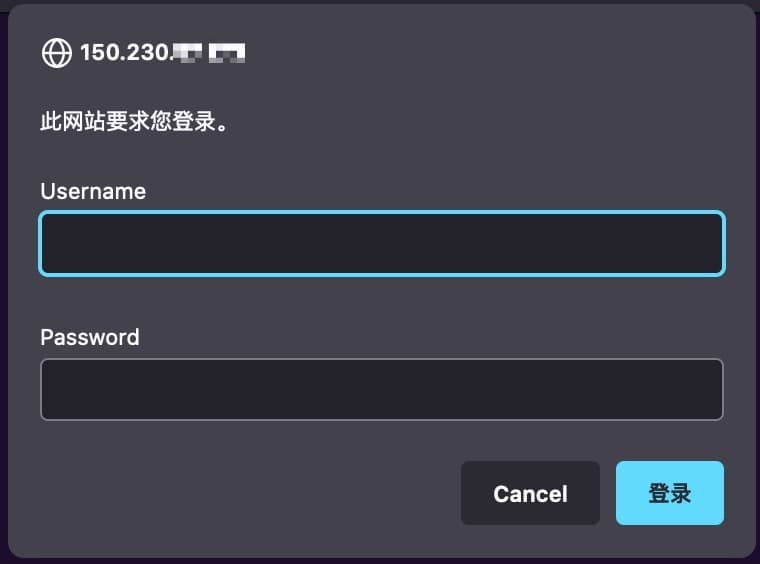
auth_basic "Restricted Access";
auth_basic_user_file /path/to/password/file;
这里的 password file 不能自己手动写,可以借助工具 htpasswd 生成
密码内容示例:
user1:$apr1$9XzVgjMY$Jx8cUwQwU31O6v5I5n5dZ0
user2:$apr1$EgOyJgi8$TwzKAEc5m1vB/3I/8CkBF/
生成用户及密码
# 首次生成
$ sudo htpasswd -c /path/to/password/file user01
# 添加用户
$ sudo htpasswd /path/to/password/file user02
- 推荐使用目录 /etc/nginx/.htpasswd
- 需要注意文件权限,使 nginx 有权限读取
最终 Nginx 示例
server {
listen 80;
server_name 150.230.77.88;
location / {
return 301 https://$server_name$request_uri;
}
}
server {
listen 443 ssl;
server_name 150.230.77.88;
ssl_certificate "/etc/ssl/certificate.crt";
ssl_certificate_key "/etc/ssl/private.key";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
auth_basic "Restricted Access";
auth_basic_user_file "/etc/nginx/.htpasswd";
proxy_pass https://poe.com;
proxy_ssl_server_name on;
proxy_set_header Host poe.com;
proxy_set_header Connection "";
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_ssl_verify off;
}
}
2024-04-25 更新
Nginx 配置添加参数,解决 500 报错问题
报错信息
2024/04/25 03:07:11 [error] 245119#245119: *1 SSL_do_handshake() failed (SSL: error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:SSL alert number 40) while SSL handshaking to upstream, client: 180.255.76.214, server: 150.230.77.88, request: "GET / HTTP/1.1", upstream: "https://162.159.152.17:443/", host: "150.230.77.88"
2024/04/25 03:07:11 [error] 245119#245119: *1 SSL_do_handshake() failed (SSL: error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:SSL alert number 40) while SSL handshaking to upstream, client: 180.255.76.214, server: 150.230.77.88, request: "GET / HTTP/1.1", upstream: "https://162.159.153.247:443/", host: "150.230.77.88"
添加配置
proxy_ssl_server_name on;